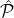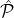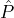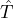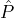4 The PoR Blockchain
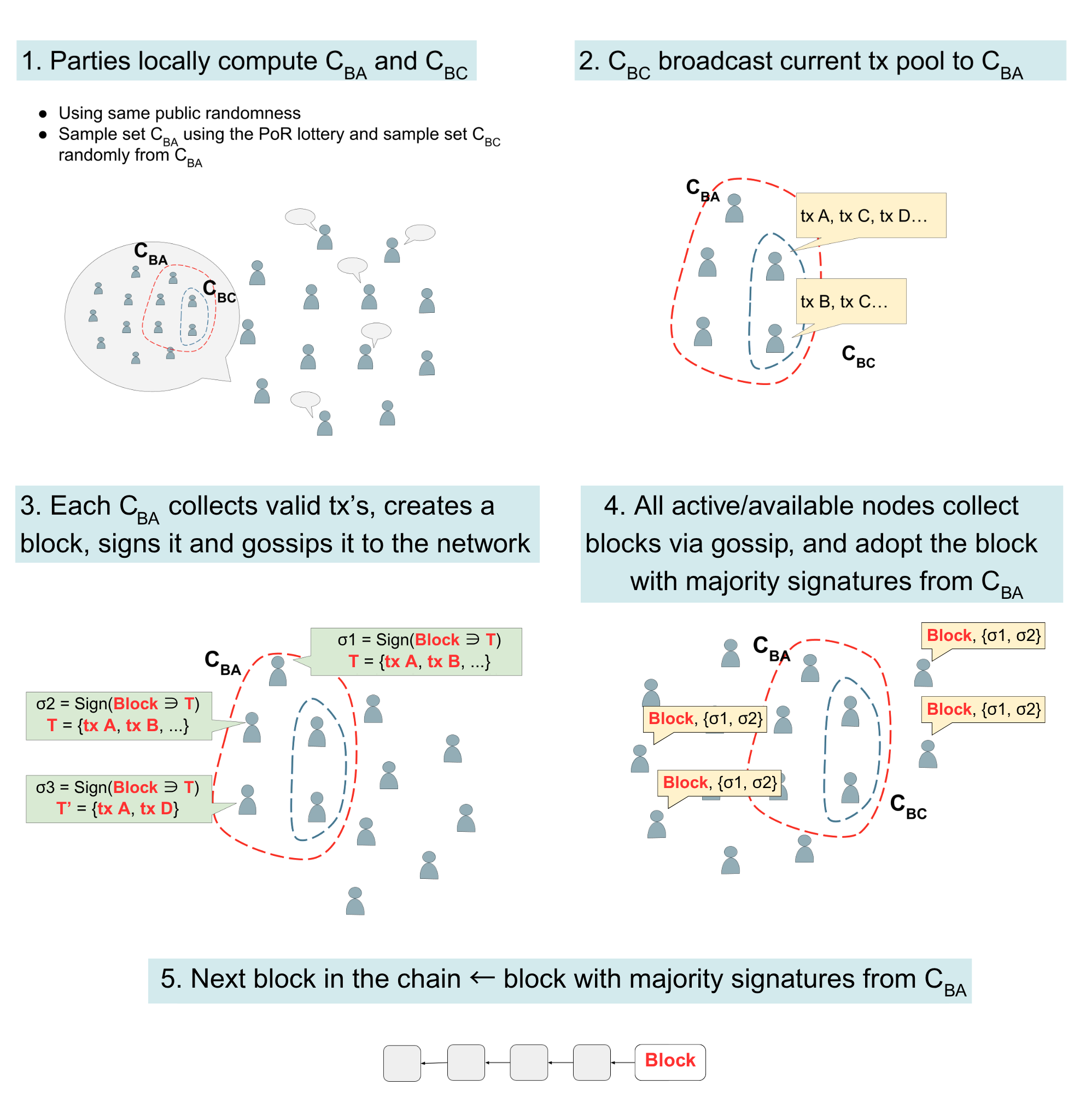
We next describe how a PoR-fair lottery can be used to obtain a PoR-blockchain. The ground truth of the 13blockchain is recorded on the genesis block which includes the (initial) set of reputation parties, their public keys, and the corresponding reputation vector. We assume a canonical way of validating transactions submitted in the same round, e.g., if two received transactions which have not-yet been inserted into a block would contradict each other (e.g., correspond to double-spending), a default rule of ignoring both can be adopted. We abstract this by means of a predicate Validate, that takes as input a sequence T (of transactions) along with a current vector TH of transaction history—composed by concatenating the transactions in the blockchain, and outputs a subset T′⊆ T such that TH||T′ is a valid sequence of transactions.
An informal description of the protocol is given in Fig.
7
. The idea of the protocol for proposing and
agreeing on
the block of any given slot is as follows: A small (i.e., polylogarithmic) slot-committee  BA is chosen using our
above lottery—recall that the lottery will guarantee that the majority in
BA is chosen using our
above lottery—recall that the lottery will guarantee that the majority in  BA is honest and therefore it can run
Byzantine agreement protocols (Consensus and Broadcast). From
BA is honest and therefore it can run
Byzantine agreement protocols (Consensus and Broadcast). From  BA a smaller (constant-size) committee
BA a smaller (constant-size) committee  BC is
randomly chosen to broadcast its transactions to everyone. Note that whenever in our protocol we say that a party
P broadcasts a message, we mean that a Byzantine broadcast protocol is executed with
P as sender; to avoid
confusion we will signify this by saying that that the message is broadcasted by means of protocol Broadcast. We
will use multicasting to refer to the process of sending a message through the diffusion
network to all
parties.
BC is
randomly chosen to broadcast its transactions to everyone. Note that whenever in our protocol we say that a party
P broadcasts a message, we mean that a Byzantine broadcast protocol is executed with
P as sender; to avoid
confusion we will signify this by saying that that the message is broadcasted by means of protocol Broadcast. We
will use multicasting to refer to the process of sending a message through the diffusion
network to all
parties.
Using Broadcast to communicate the transactions known to  BC allows us to agree on the union
of all transactions known to these parties. However, broadcasting to the whole player set has a big
communication and round overhead. To avoid the overhead we use the following idea: Recall that the
parties in
BC allows us to agree on the union
of all transactions known to these parties. However, broadcasting to the whole player set has a big
communication and round overhead. To avoid the overhead we use the following idea: Recall that the
parties in  BA are all reputation parties and can therefore
communicate directly. Thus, instead of
directly broadcasting to the whole party set
BA are all reputation parties and can therefore
communicate directly. Thus, instead of
directly broadcasting to the whole party set  the parties in
the parties in  BC broadcast to the parties in
BC broadcast to the parties in  BA.
14 The
security of the broadcast protocol ensures that the parties in
BA.
14 The
security of the broadcast protocol ensures that the parties in  BA agree on the broadcasted messages and therefore
also on the union. What remains is to extend this agreement to the whole player set. This can be easily done since
the majority of the parties in
BA agree on the broadcasted messages and therefore
also on the union. What remains is to extend this agreement to the whole player set. This can be easily done since
the majority of the parties in  BA is honest: Every party in
BA is honest: Every party in  BA signs the union of the received broadcasted
messages and sends it to every party in
BA signs the union of the received broadcasted
messages and sends it to every party in  . The fact that
. The fact that  BA has honest majority implies that the
only message that might be accepted is this agreed upon union. Hence, once any P ∈
BA has honest majority implies that the
only message that might be accepted is this agreed upon union. Hence, once any P ∈ receives such
a majority-supported set, he can adopt it as the contents of this slot’s block. The above approach
brings an asymptotic reduction on the communication complexity of the protocol from Ω(n2) down
to O(nlog ϵn), for some constant ϵ > 1. (The worst-case round complexity also has an asymptotic
reduction but this depends on the actual reputation system and the choice of protocol Broadcast.)
Additionally, the fact that reputation parties communicate over point-to-point (rather than gossiping) network
is likely to further to improve the concrete communication complexity, at least for certain network
topologies.
receives such
a majority-supported set, he can adopt it as the contents of this slot’s block. The above approach
brings an asymptotic reduction on the communication complexity of the protocol from Ω(n2) down
to O(nlog ϵn), for some constant ϵ > 1. (The worst-case round complexity also has an asymptotic
reduction but this depends on the actual reputation system and the choice of protocol Broadcast.)
Additionally, the fact that reputation parties communicate over point-to-point (rather than gossiping) network
is likely to further to improve the concrete communication complexity, at least for certain network
topologies.
A remaining question is: Where does the randomness for the selection of  BA and
BA and  BC come from? For the
static reputation-restricted adversary considered here, we extract the randomness for choosing each
BC come from? For the
static reputation-restricted adversary considered here, we extract the randomness for choosing each  BA by
repeated calls to the random oracle. In the appendix we discuss how we can extend our treatment using standard
techniques to tolerate epoch-resettable adversaries. The formal description of the protocol for announcing and
agreeing on the next block can be found in Figure
8
. The proof of the following theorem follows the
above line of
argument and can also be found in Appendix
C.2
.
BA by
repeated calls to the random oracle. In the appendix we discuss how we can extend our treatment using standard
techniques to tolerate epoch-resettable adversaries. The formal description of the protocol for announcing and
agreeing on the next block can be found in Figure
8
. The proof of the following theorem follows the
above line of
argument and can also be found in Appendix
C.2
.
|
|
|
|
BlockAnnounce(
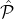 , ,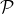 ,Rep,Bρ-1,ρ,δ,ϵ,L = O(1)): ,Rep,Bρ-1,ρ,δ,ϵ,L = O(1)):
|
|
|
|
|
Theorem 2. Let Rep be a reputation system, ϵ and δ be small positive constants, L denote our sampling
algorithm (lottery) discussed in the previous section used for choosing  BA according to Rep, and the ci’s
be as in Theorem
1
. If for a static adversary
BA according to Rep, and the ci’s
be as in Theorem
1
. If for a static adversary  , Rep is ϵ-feasible, and all parties in
, Rep is ϵ-feasible, and all parties in 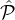 ρ participate in slot
ρ then in protocol BlockAnnounce, every node in
ρ participate in slot
ρ then in protocol BlockAnnounce, every node in  adds the same block on his local blockchain for slot ρ.
Moreover, this block will include the union of all transactions known to parties in
adds the same block on his local blockchain for slot ρ.
Moreover, this block will include the union of all transactions known to parties in  BC at the beginning of
round ρ.
BC at the beginning of
round ρ.
Using BlockAnnounce it is straightforward to build a blockchain-based ledger: In each round parties collect all valid transactions they know and execute BlockAnnounce. For completeness, we provide a description of this simple reputation-based blockchain ledger protocol in Appendix B . Its security follows directly from the above theorem. We remark that although the above theorem is proven for static reputations and adversaries, its proof can be extended, using standard techniques, to dynamic reputation systems with epoch-resettable adversaries. This extension will also extend the corresponding PoR-based blockchain protocol to that setting.
14 For clarity in our description we will use a deterministic broadcast protocol for Broadcast, e.g., the Dolev-Strong
broadcast protocol [43] for which we know the exact number of rounds. However, since our lottery will ensure honest
majority in  BA, using the techniques by Cohen et al. [37, 38], we can replace the round-expensive Dolev-Strong
broadcast protocol by an randomized, expected-constant round broadcast protocol for honest majorities,
e.g., [63].↩
BA, using the techniques by Cohen et al. [37, 38], we can replace the round-expensive Dolev-Strong
broadcast protocol by an randomized, expected-constant round broadcast protocol for honest majorities,
e.g., [63].↩
a As is common in blockchains assuming a compact representation of the block, e.g., a Merkle-tree will allow for more efficiency by signing just the root.↩