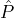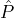F Epoch-Resettable Adversaries
We can also extend our analysis for announcing the blocks in each slot, and thereby our ledger protocol, to cope with epoch-resettable adversaries. In fact, as long as the reputation system ensemble is a sequence of independent (static) reputation systems, we do not need to make any modification to the protocol other than requiring the parties to refresh their key in each epoch; this can be done interactively, by posting a new key on the blockchain in every epoch and erasing the previous key, or non-interactively by using a forward secure signature scheme [21, 58]. Indeed, although the epoch-resettable adversary will able to predict the next epoch’s committees, he is still bound to select his corrupted parties independently according to their (new) reputation. As long as all reputation vectors (i.e., for each epoch) are feasible, such an adversary will be unable to have a corrupted majority committee chosen, except with negligible probability.
However the above assumption that reputation-vectors of different epoch are independent,
might fall short in capturing situations, where malicious parties might try to manipulate their
reputation (e.g., by temporarily playing honestly) depending on the protocol’s history. Under the
assumption that reputation for the next epoch is already define in the one-but-last slot of the current
epoch16
we can tolerate an epoch-resettable adversary by modifying the way this randomness is selected as follows: We adapt
the block announcing protocol to have every party in any committee include, in addition to his transaction pool, a
fresh random nonce, and the concatenation of all these nonces is included to the block along with the
union of the transactions posted by  BC. (The corresponding protocol is given in Figure 14). As the
distribution of the reputation vector is decided before the last slot, the choice of all parties in the
next epoch will be independent of this distribution and therefore the same guarantees as before will
apply.
BC. (The corresponding protocol is given in Figure 14). As the
distribution of the reputation vector is decided before the last slot, the choice of all parties in the
next epoch will be independent of this distribution and therefore the same guarantees as before will
apply.
|
|
|
|
BlockAnnounce(
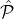 , ,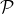 ,Rep,Bρ-1,ρ,δ,ϵ,L = O(1)): Let ,Rep,Bρ-1,ρ,δ,ϵ,L = O(1)): Let 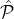 ρ denote the reputation parties in Slot ρ. ρ denote the reputation parties in Slot ρ.
|
|
|
|
|
Unfortunately, the above idea is still problematic. Indeed, since with an epoch resettable adversary the corrupted set is “reset” at the beginning of each epoch, the adversary across two epochs might be able to take keys he learned in the first of the two epoch and use them at the beginning slot of the second epoch (before parties have had a chance to erase) thereby effectively holding the keys of a majority of the parties in the latter epoch, even when both epoch’s reputation systems are ϵ-feasible.
To counter this scenarios, we consider the following strengthening of the notion of ϵ-feasibility:
Definition 5. For a reputation system Rep for parties from a reputation set 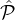 , a
(possibly probabilistic) algorithm A for sampling a subset of parties from
, a
(possibly probabilistic) algorithm A for sampling a subset of parties from 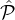 , and an
Rep-adversary
, and an
Rep-adversary  , we say that Rep is strongly (ϵ,A)-feasible for
, we say that Rep is strongly (ϵ,A)-feasible for  if, with overwhelming
probability,17
A outputs a set of parties such that at most a 1∕4 - ϵ fraction of these parties is corrupted by
if, with overwhelming
probability,17
A outputs a set of parties such that at most a 1∕4 - ϵ fraction of these parties is corrupted by  .
.
Note that in the above definition, the corrupted parties are chosen according to Rep from the entire
reputation-party set 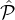 , and independently of the coins of A. (Indeed, otherwise it would be trivial to always corrupt
a majority.)
, and independently of the coins of A. (Indeed, otherwise it would be trivial to always corrupt
a majority.)
Definition 6. We say that a reputation system is strongly ϵ-feasible for Rep-adversary  , if there exists a
probabilistic polynomial-time (PPT) sampling algorithm A such that Rep is strongly (ϵ,A)-feasible for
, if there exists a
probabilistic polynomial-time (PPT) sampling algorithm A such that Rep is strongly (ϵ,A)-feasible for  .
.
It is easy to verify that if the reputation systems corresponding to all epochs are strongly ϵ-feasible, then the probability that the adversary in two consecutive epochs can launch the above attach (i.e., using the keys learned in the first of the two epochs exceed a minority of corruptions in the second one) is negligible. This is true as long as the two epochs have the same (distribution on the) size of committees, since even if all corrupted parties from the first epoch are selected in the second one, still the adversary will not be able to reach more than a minority of corruptions (since in each epoch at most 1∕4 - ϵ fraction is corrupted).
Since in each epoch the adversary needs to release the parties from the previous epoch which are not newly corrupted, we can have the parties refresh their signing keys in each epoch—either by erasing the old keys and posting new ones on the blockchain or by using a forward-secure signature scheme—thereby ensuring that the adversary can never corrupt a majority. It is easy to verify that the above modification ensures security of our construction against epoch-resettable adversaries.
16 This is a natural assumption as any reputation adjusting mechanism will need to have parties agree on the adjustment of the reputation, e.g., by extracting is from blocks deep enough in the blockchain.↩